Deploy and Configure Unified Access Gateway
VMware Unified Access Gateway (UAG) is an appliance that acts as a security gateway for the internal network. It is normally installed in a demilitarized zone (DMZ) to ensure that the only traffic entering the corporate data center is traffic on behalf of a strongly authenticated remote user to enable secure remote access from an external network to a variety of internal resources for end users.
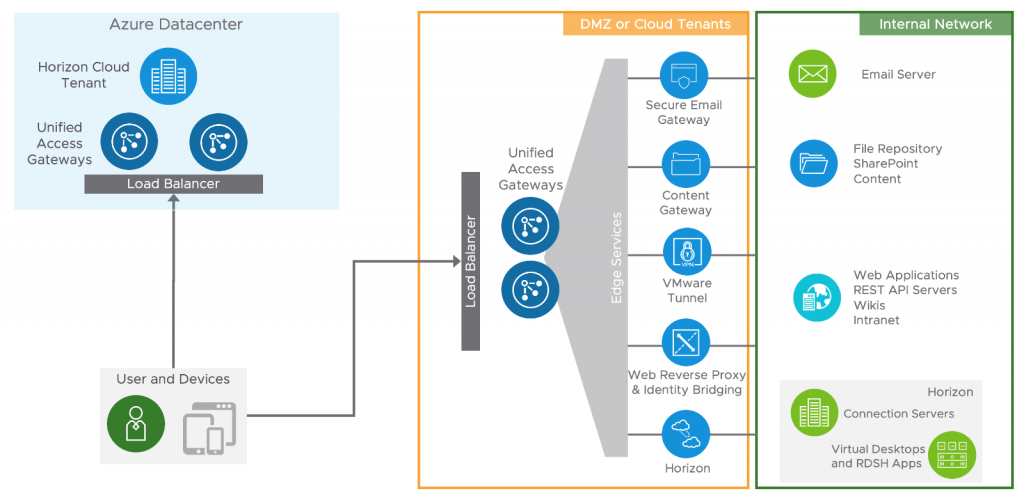
Unified Access Gateway or UAG is the key to VMware Horizon and Workspace ONE deployment, it provides multiple essential services for different use cases and protocols, including:
- Secure access to Horizon virtual desktops and applications
- Secure access to internal resources (VMware Tunnel)
- Secure access to internal websites (Web Reverse Proxy)
- Secure access to internal file shares or SharePoint repositories (Content Gateway)
- Secure access to email infrastructure (Secure Email Gateway)
Horizon 8 Series:
- Overview Horizon
- Install Horizon Connection Server
- Horizon Initial Configuration
- Deploy an Instant-Clone Desktop Pool
- Deploying Published Desktops and Applications
- Update an Instant-Clone Desktop Pool
- Configure Dynamic Environment Manager
- Deploy and Configure Unified Access Gateway
- Configure Workspace ONE Access – Part 1
- Configure Workspace ONE Access – Part 2
- Configure Workspace ONE Access – Part 3
This post will show you how to install and configure UAG for your environment.
Deploy Unified Access Gateway OVF
There are two ways to deploy the UAG: manually deploying the OVA through vCenter or using Powershell to automate the process. In this example, I prefer to deploy the OVA manually via vCenter.
1- Download the VMware Unified Access Gateway 2209 OVA file.
There are two versions of the Unified Access Gateway OVA, Non-FIPS version and FIPS version. Normally you need the non-FIPS version.

2- After downloading the OVF file, log in to vCenter, right-click Cluster, and select Deploy OVF Template.
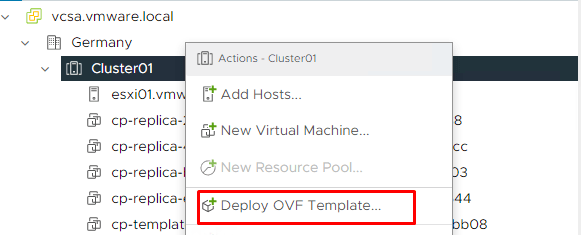
3- On the Select an OVF Template page, select the Local file and click Upload files. Navigate to the downloaded file and click Open. The selected file will be displayed and click Next.
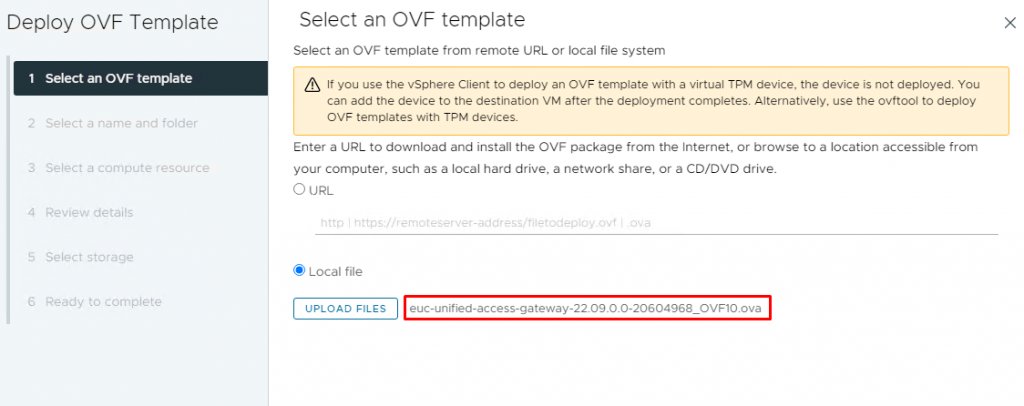
4- Give a proper name and select a folder for the virtual machine and click Next.
5- On the Select a compute resource page, select a host or cluster and click Next.
6- On the Review Details page, click Next.
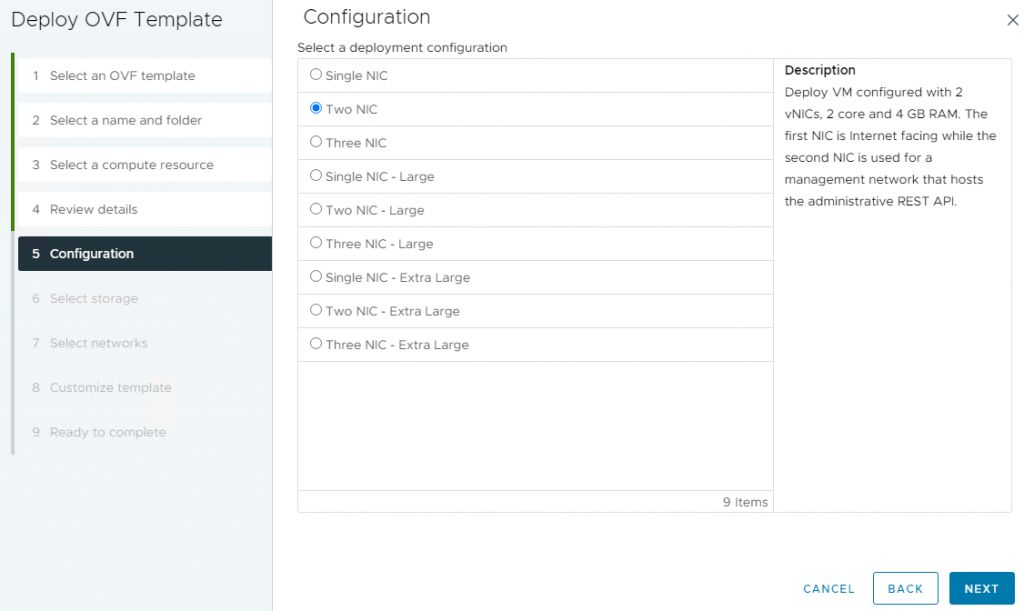
7- On the Configuration page, select your desired deployment configuration and click Next. Unified Access Gateway supports deployments with one, two, or three Network Interface Cards (NICs).
- The simplest deployment of UAG is with a single NIC, where all network traffic is aggregated into a single network.
- The two NICs separate unauthenticated user traffic from backend and management traffic.
- The three NICs separate all traffic from each other.
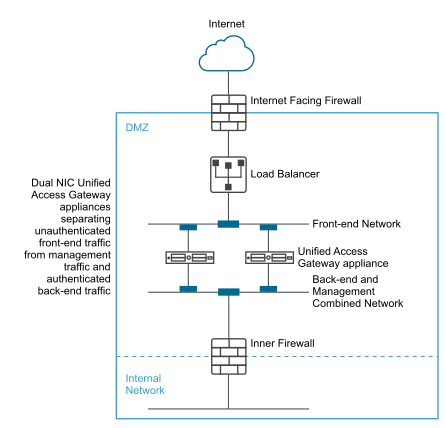
You can find more info about the type of deployment configuration here. In a two-NIC deployment as shown in the picture above, One NIC is used for unauthenticated Internet access or External network and the other NIC is used for authenticated back-end and management traffic. This type of deployment is suitable for production environments. I have also chosen this type of configuration for this example.
8- On the Select storage page, select virtual disk format and a data store and then click Next.
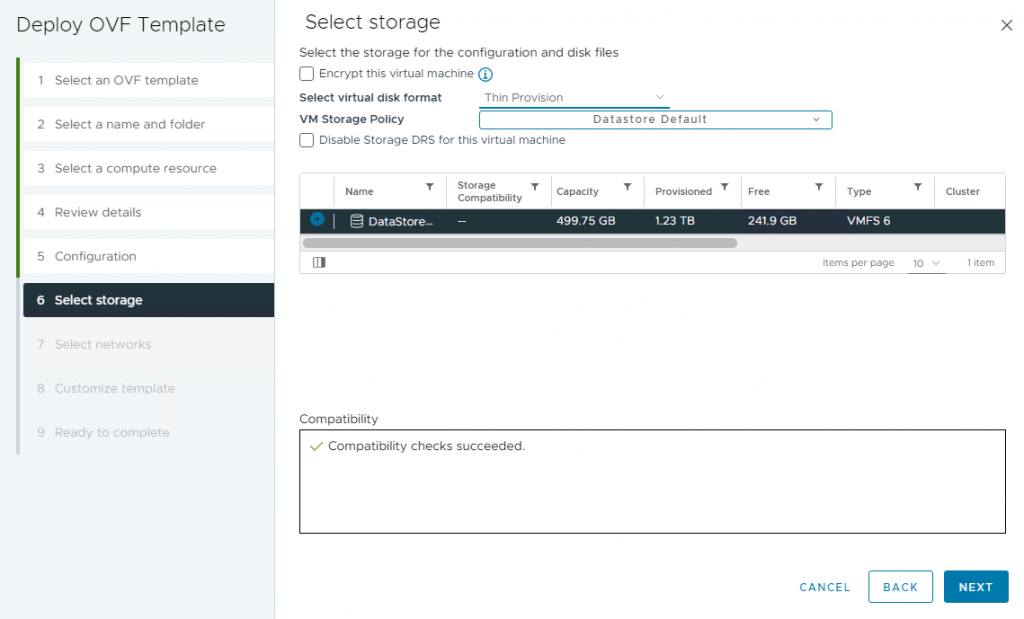
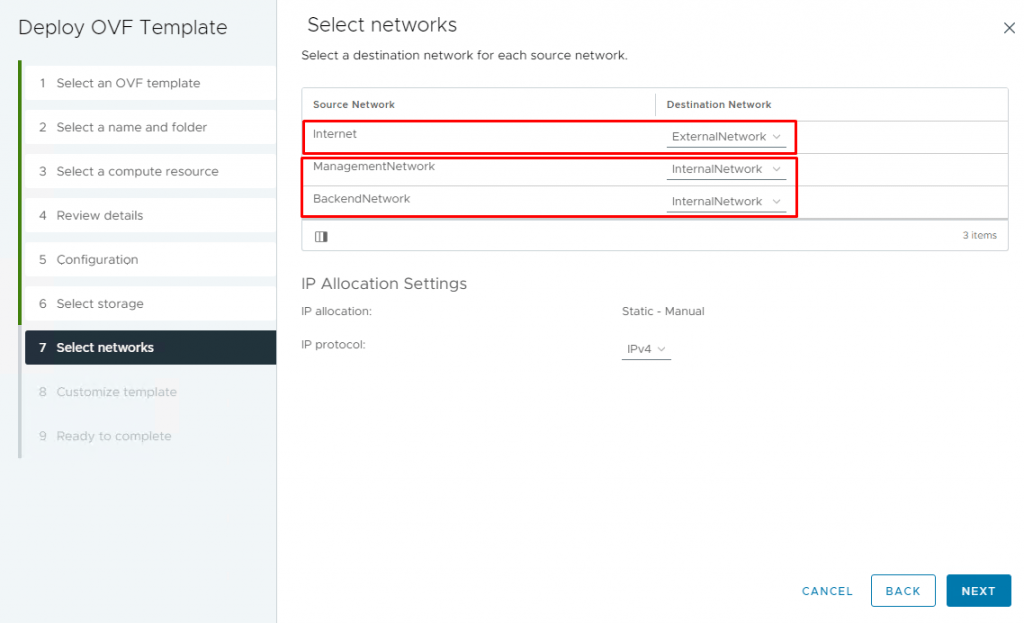
9- On the Select networks page, select the destination of each source and click Next. Because I selected Two-NIC configurations, the Internet should go through one NIC, and management and backend traffic should go through another NIC.
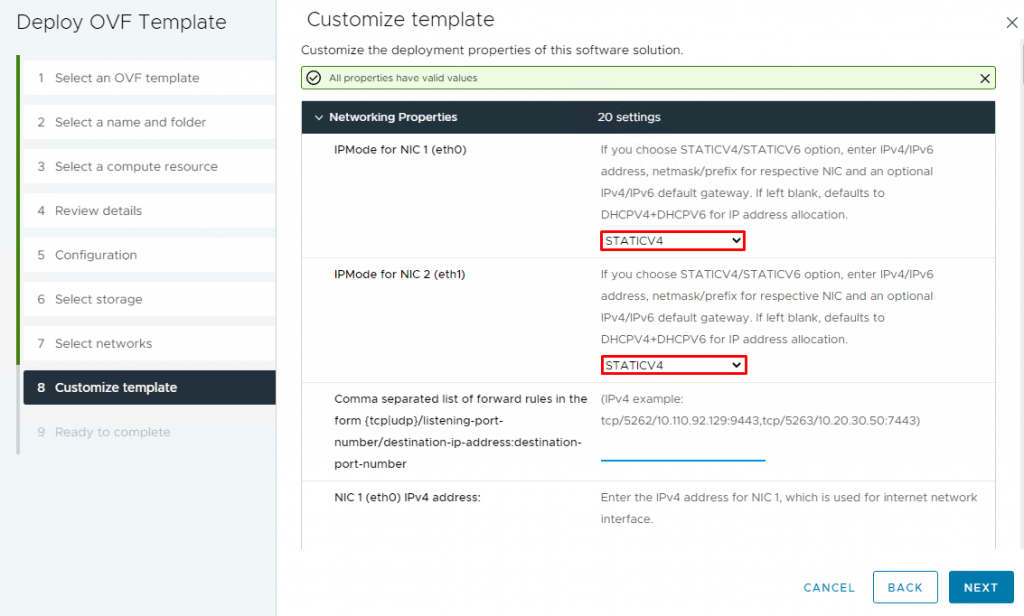
10- On the Customize template page, set IPMode STATICV4 for NIC1 and NIC2 and scroll down.
11- Enter the IPv4 address of NIC1 (eth0) used for the internet network (external network) interface and scroll down.
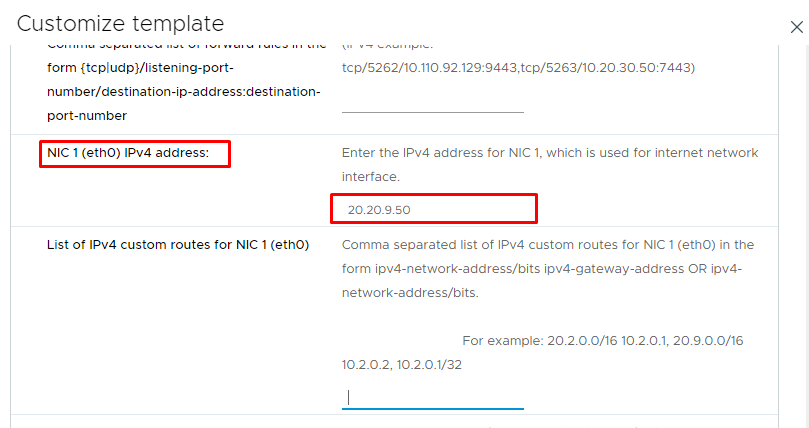
12- Enter DNS addresses, Subnet Mask, and Default Gateway. (I pointed to the internal DNS server, which is located in the DMZ)
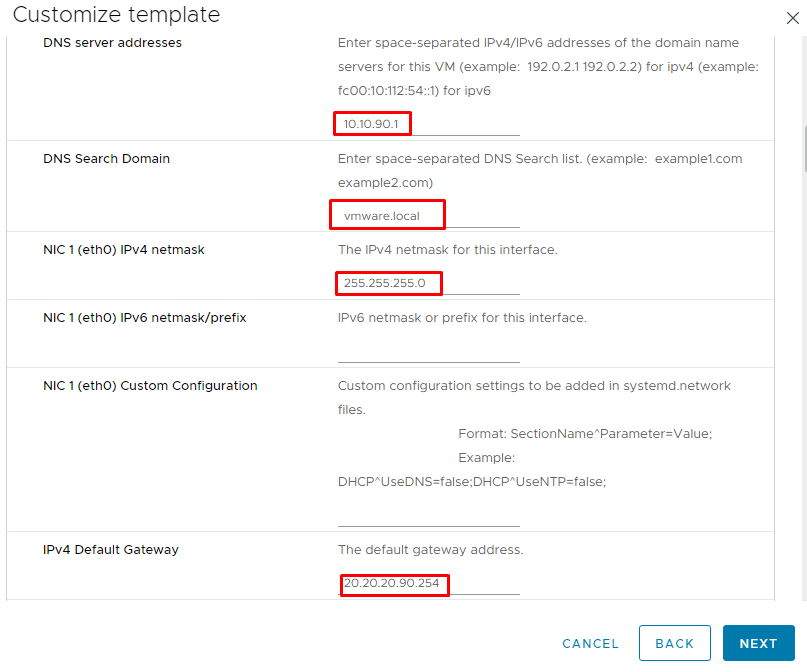
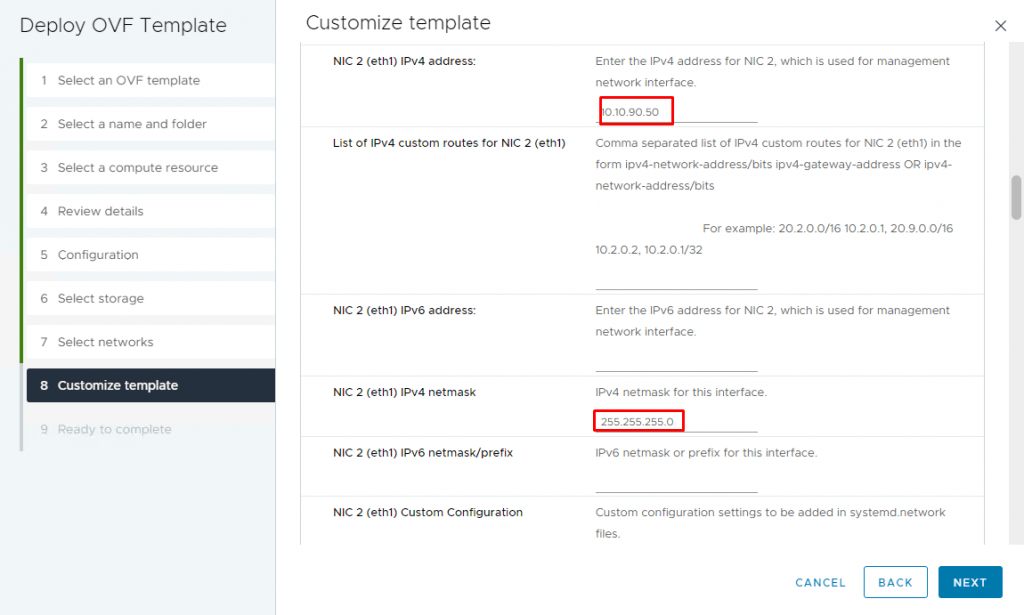
13- Enter the IPv4 address of NIC2 (eth1) used for the management and backend network interface and scroll down.
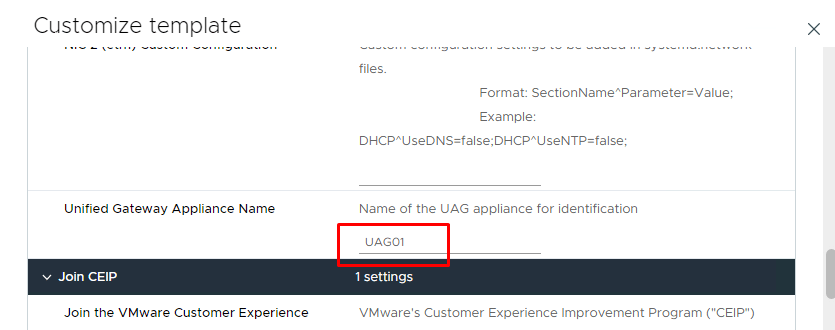
14- Enter the Unified Gateway Appliance Name and scroll down.
15-Specify a username and password for the UAG VM for access to the console and scroll down.
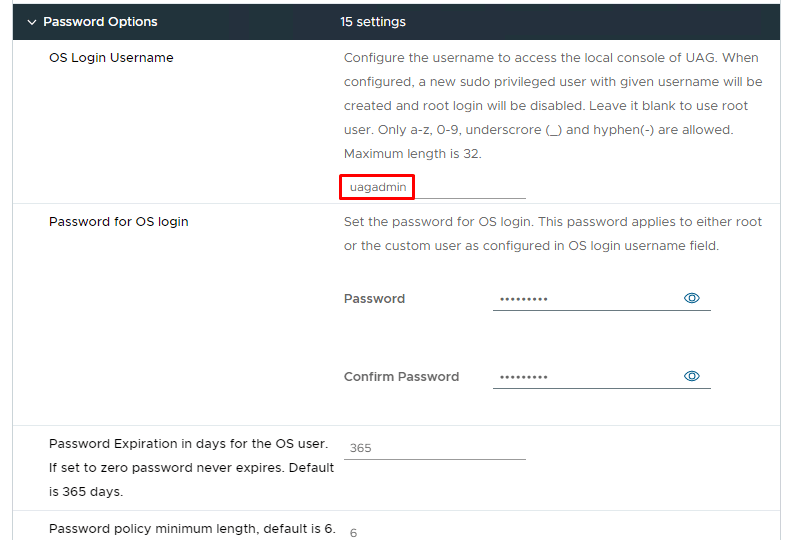
16- Enter the password for the admin user.
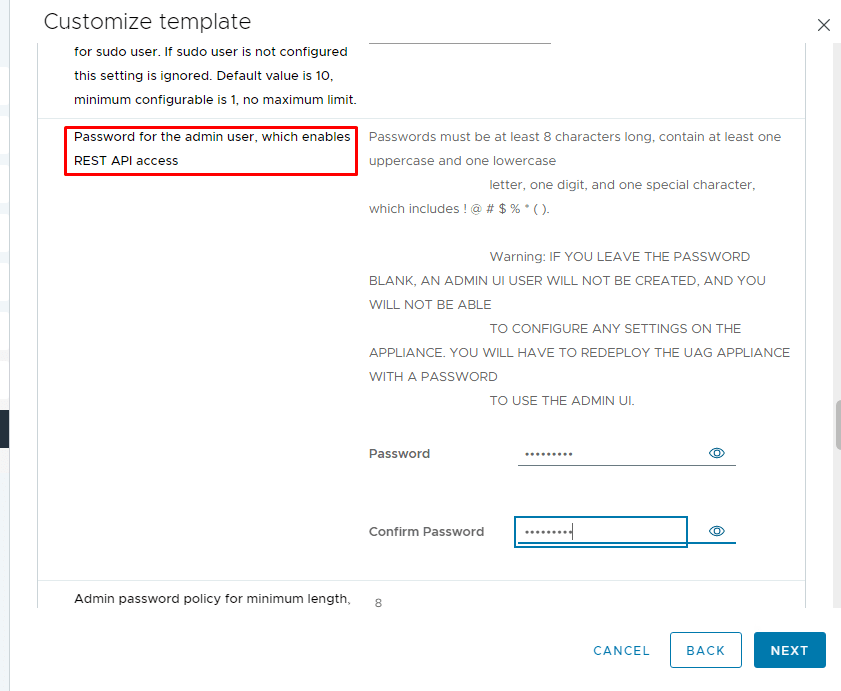
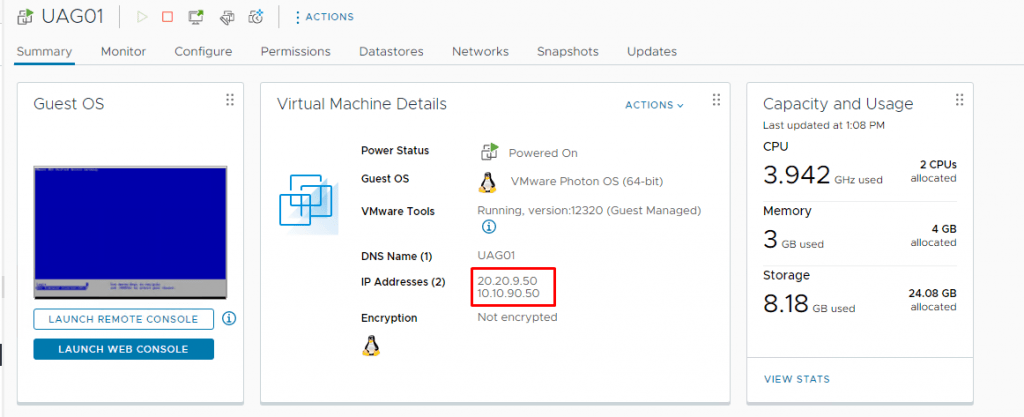
17- Leave other settings as default and click Next and then Finish. After the virtual machine is deployed successfully, power it on. It should detect both IP addresses you entered during deployment.
Configure Unified Access Gateway
1- Access to the UAG Administration Console Login using the IP address of UAG with port 9443.
Https://IP of UAG:9443/admin/index.html
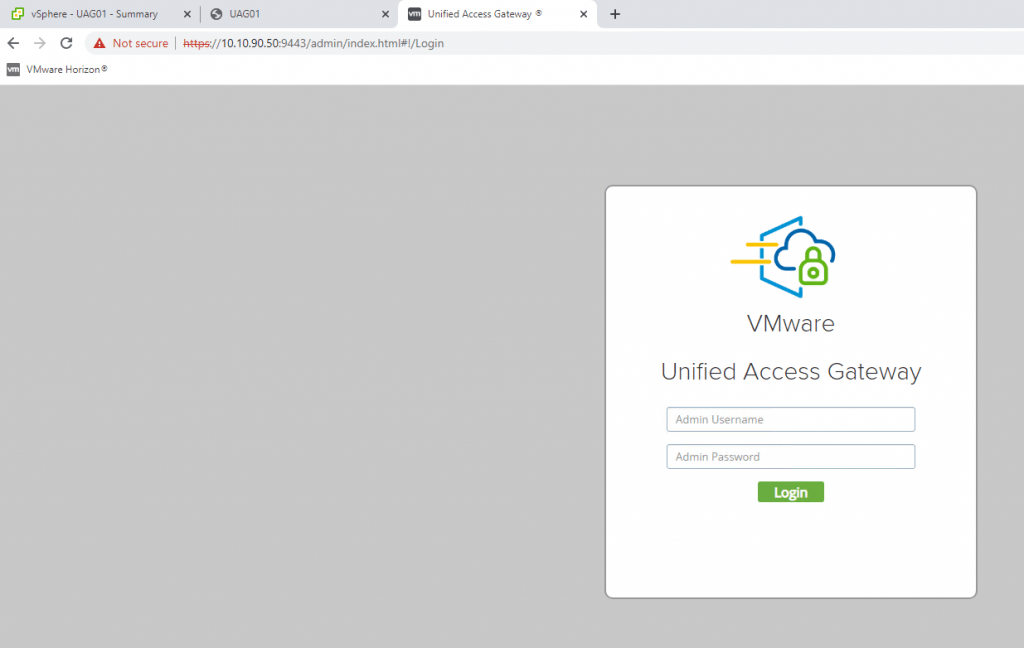
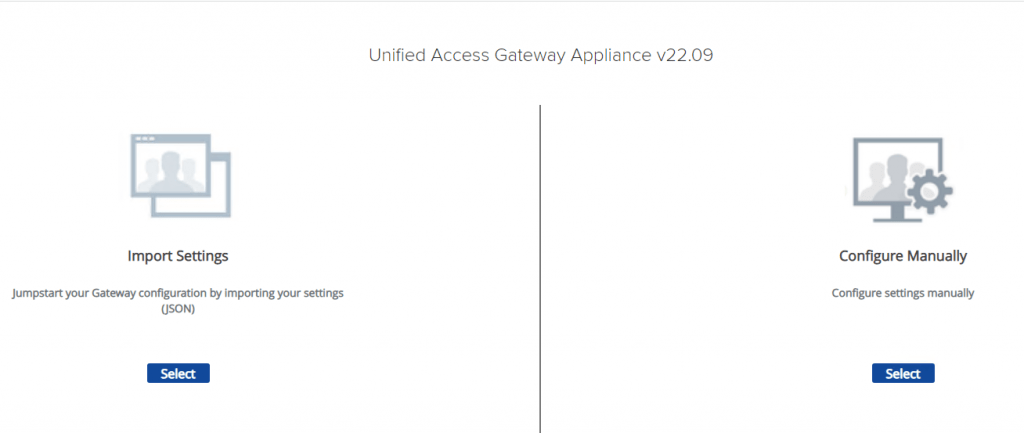
2-Log in with the admin user and the password you entered during deployment. After A successful login, you redirect to the window where you can import settings or manually configure the UAG appliance. Click Select under Configure Manually.
3- Under General Settings, click on the show toggle next to Edge Service Settings, it switches to green after you clicked, and then click the gear icon next to Horizon Settings.
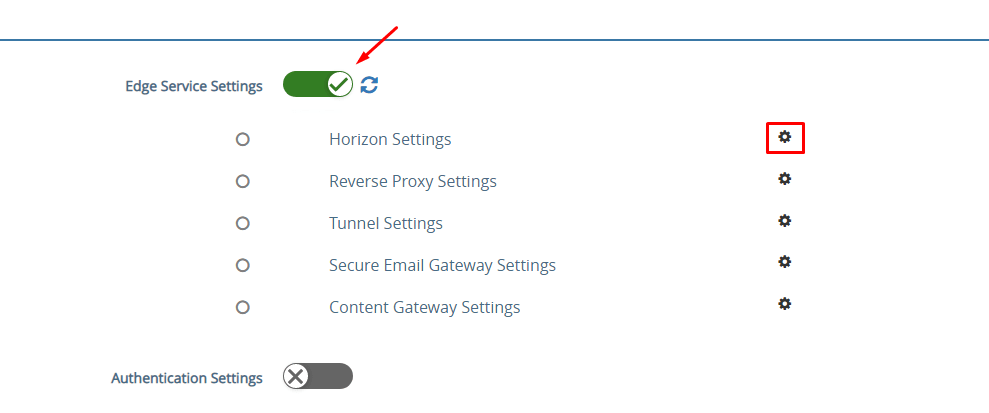
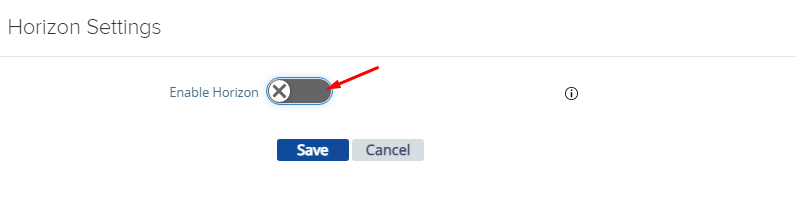
4- Enable Horizon and configure the following parameters and click Save.
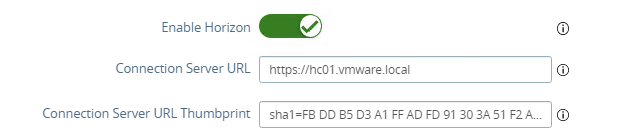
- In the Connection Server URL field, enter the FQDN of the connection server or load balancer if your connection server is behind the load balancer. Since my domain contains .local and it appears that the new systemd-resolved method uses .local exclusively for multicast DNS, I need to edit resolve.conf. For more information and instructions visit this link.
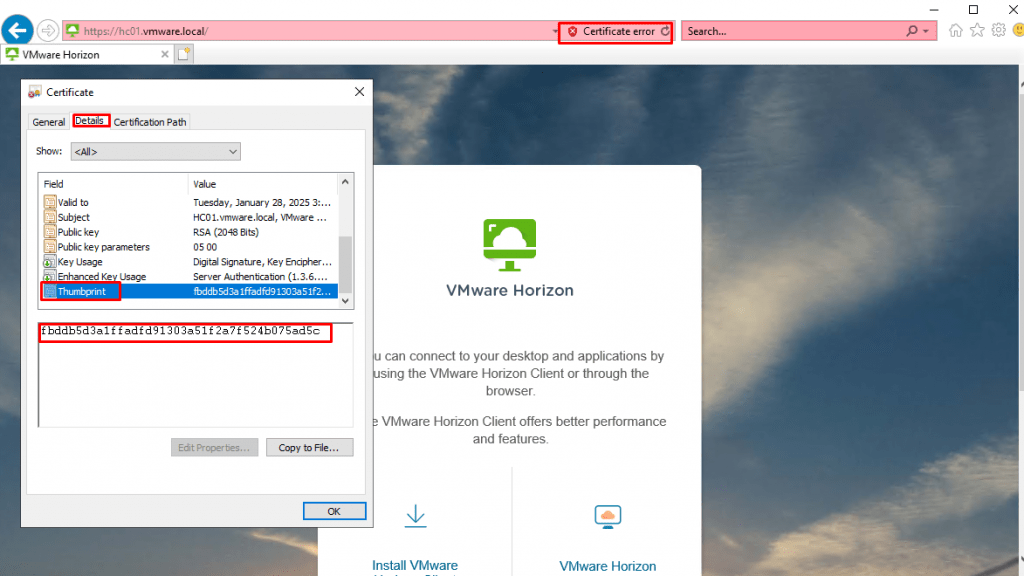
- In the Connection Server URL Thumbprints field, enter “
sha1=Horizon CertificateThumbprint“. To obtain the thumbprint, browse to the Horizon Connection and click the certificate to open the certificate properties, on the Details tab, you can find the thumbprint.
- Enable PCoIP, Blast, and Tunnel.
- In the PCoIP External URL field, enter the external IP address of UAG with the port number (4172). If you are using a load balancer to balance between multiple UAGs, enter the IP address of the load balancer. Clients that use the PCoIP display protocol can use the PCoIP Secure Gateway.
- In the Blast External URL field, enter the FQDN of the load balancer or UAG (https://:8443). It enables users to make secure connections through Blast Secure Gateway.
- In the Tunnel External URL field, enter the FQDN of the load balancer or UAG (https://:443). Clients that use the RDP display protocol can use the secure tunnel.

5- After you click the Save button, all items should be GREEN, indicating that the appliance can communicate with the Horizon Connection Server using the various configured protocols.
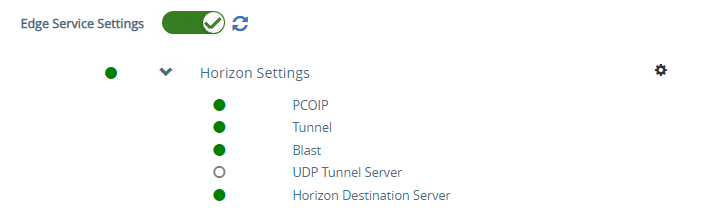
6. When you are using UAG, you need to disable the secure gateways on the Connection Server and enable these gateways on the UAG. I have enabled gateways on UAG right now, So I just need to disable them on the Connection Server. In Horizon Administrator Console, navigate to Settings, Servers, and Connection Server, select your Connection Server, and click the Edit button.
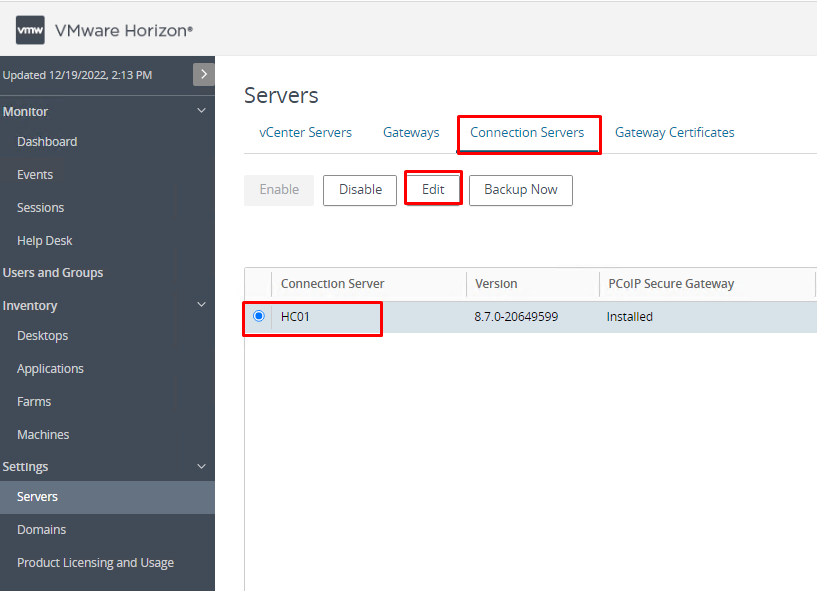
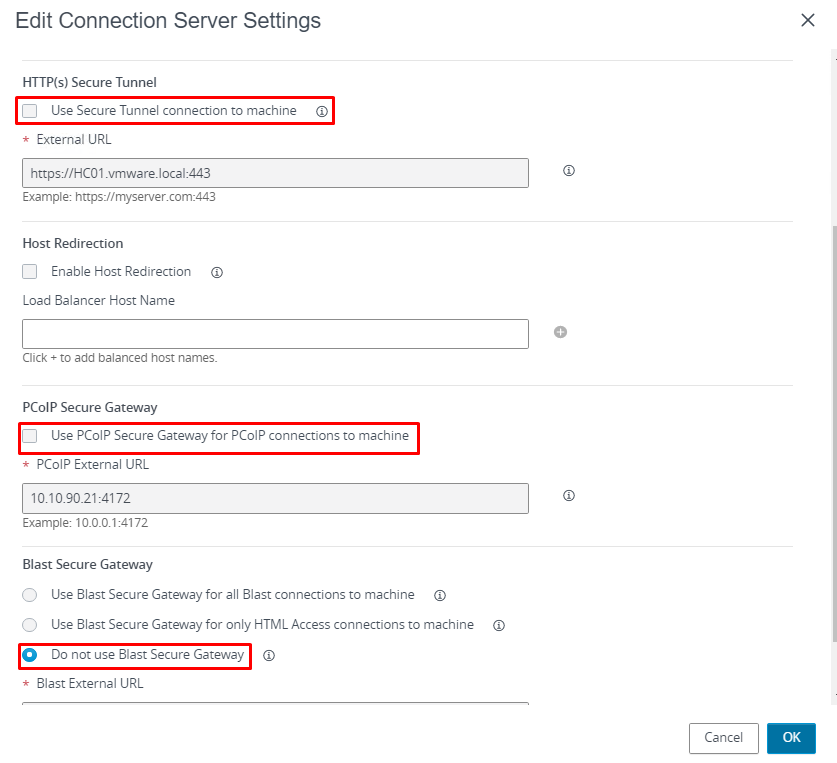
7- Uncheck the following options and select “Do not use Blast Secure Gateway” and click OK.
- Use Secure Tunnel connection to machine
- Use PCoIP Secure Gateway for PCoIP connections to machine
8- Try to access Horizon from outside the internal network by using the FQDN of the load balancer or UAG. You can connect through VMware Horizon Client or a browser. You should probably receive the following error message when you try to access it.
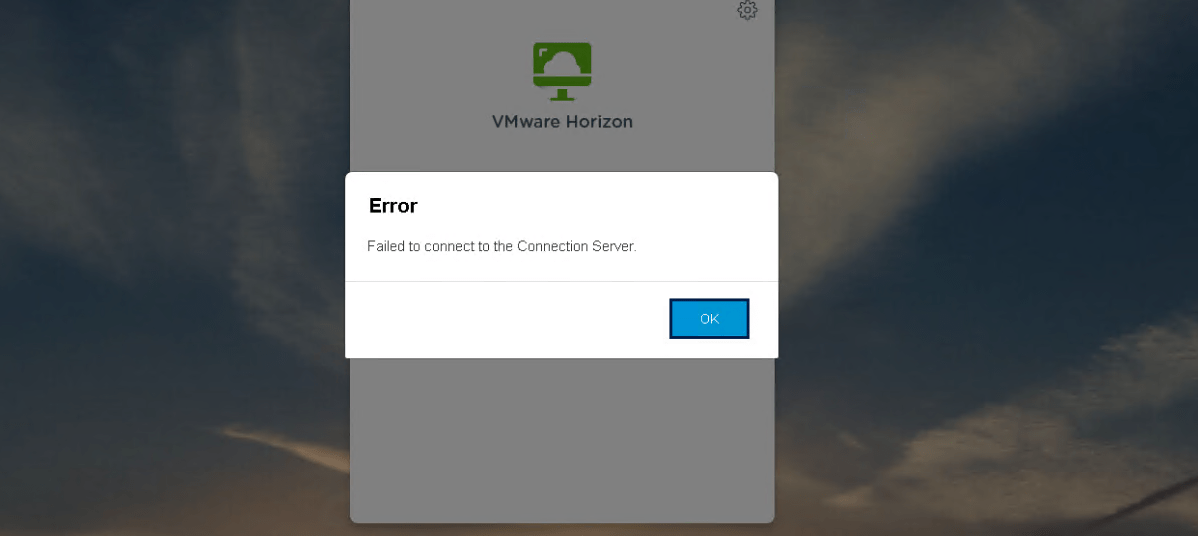
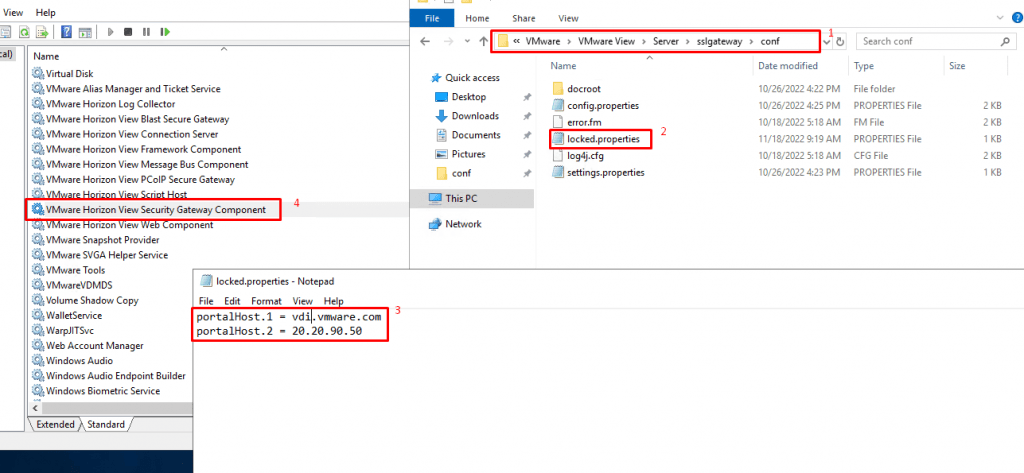
The reason for this error is that the URL that users (or you) are trying to connect, must be included in the list of known origins for each connection server. This list can be edited by logging into the server acting as Horizon Connection, stopping the “VMware Horizon View Security Gateway Component” and then editing the locked.properties file at this address: “C:\Program Files\VMware\VMware View\Server\sslgateway\conf” (this is the default location) and then restarting the service. In this example, my external IP address and external FDQN need to be added to this list. You can find more information about this error in this link.
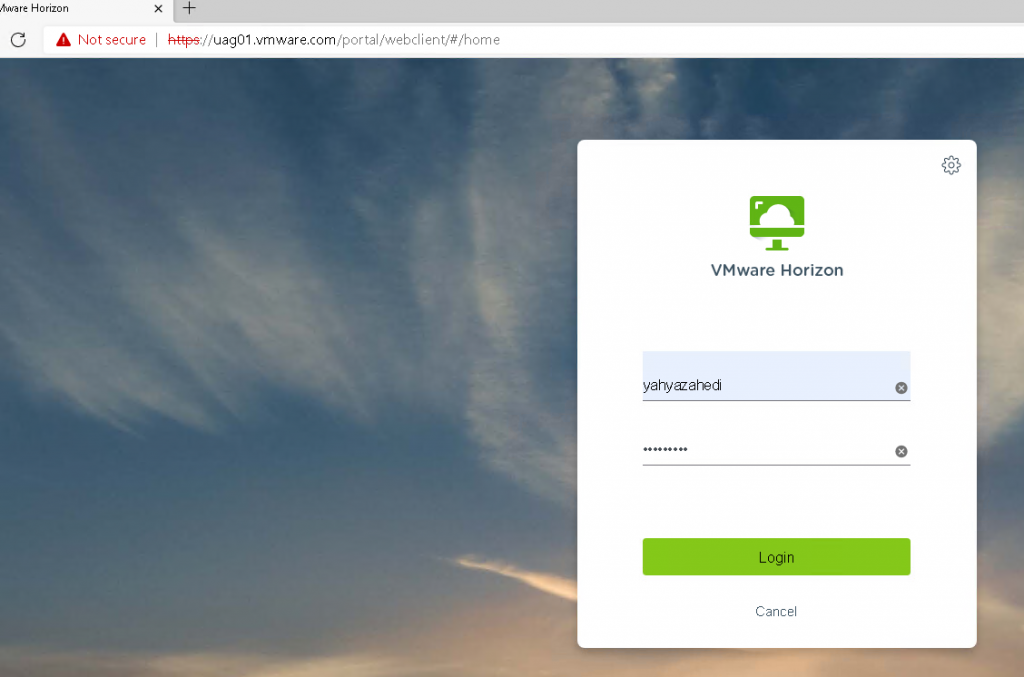
9 -As you can see, this time I can access the external URL of UAG without any problem. I logged in to Horizon desktop with an authorized user.
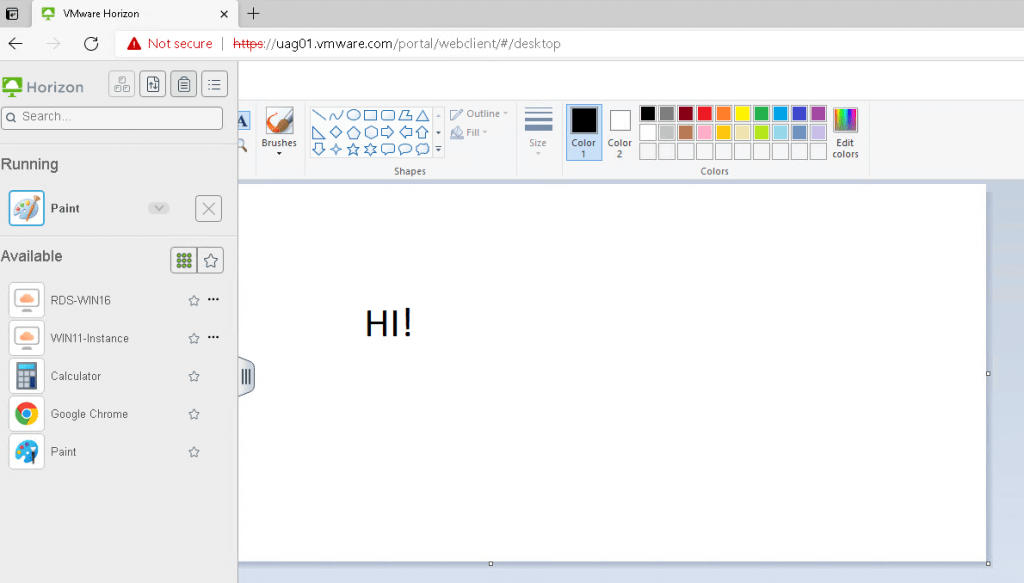
It worked and I can see the list of applications and desktops available.
I hope this is informative for you. If you have any questions, please do not hesitate to contact me.
























Good afternoon. I just saw your blog and I’m very interested in setting up my own UAG.. I saw a lot of tutorials online but none of them can take you from setting up up ip addresses, firewall rules to the deployment for external uses of an UAG. I mean the complete and detailed step by step one. Could you give some advices.. where to start.? By the way, I have working connection server running in my home lab. I trying to setup like a production UAG for school purposes…Thanks.
Hello, if you are looking for in-depth article that I don’t think you can find in one post, I would recommend you to follow this page. It is a great resource that I have used for this post and my projects.
https://docs.vmware.com/en/Unified-Access-Gateway/2203/uag-deploy-config/GUID-F5CE0D5E-BE85-4FA5-BBCF-0F86C9AB8A70.html